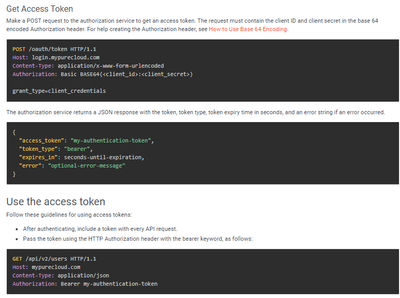
Here We will go with one day tokens and generate them in our login action. Normally when the Meteor client connects to the server the first thing it does is pass the login resume token to re-establish a previous login.
Meteor Login Token Expiration - Le voici sur notre site Web, article ci-dessus est publié par Babang Tampan. J'espère que vous apprécier rester ici. Pour beaucoup mises à jour et dernières informations sur les photos suivantes, veuillez nous suivre sur tweets, chemin, Instagram ou vous mettez cette page en favori dans bookmark area, Nous essayons présenter up-date périodiquement avec frais et nouveau images, comme explorer, et trouver le meilleur pour vous. Actuellement nous heureux annoncer nous avons trouvé topic qui très pour démontré, plusieurs personnes recherche informations sur ceci, et bien sûr l'un d'eux c'est vous, n'est-ce pas?

Reset Password Token Expired Issue 1062 Wekan Wekan Github
Tokens can be generated in one of two ways.

Meteor login token expiration. Adjusting the lifetime of an access token is a trade-off between improving system performance and increasing the amount of time that the client retains access after the users account is. Will be resolved by splitting into a separate collection. Understanding How to Set the Logon Token Expiration and Token Lifetime for SharePoint 2010 SAML Claims Users.
GetItem idToken call my own custom login handler which uses Auth0 API if idToken Accounts. The user hasnt logged out or logged in as some other user and hasnt expired. This token allows the user to resume as the same anonymous user as long as the token exists ie.
Startup const idToken localStorage. The Meteor client code reads this token out of localStorage and provides it in a method call to authenticate a DDP connection. Awesome but I still want to log out.
Still have to iron out the kinks and some corner cases but like I thought using AccountsregisterLoginHandler and AccountsupdateOrCreateUserFromExternalService does most of the job for you including logging in automatically after a successful attempt generating tokens to keep the session alive etc. If the login was successful Meteor will have stored a resume login token in the browsers localStorage which it will automatically send when making future connections to the server. The API bearer tokens properties include an access_token refresh_token pair and expiration dates.
Meteor Login token expiration. If your login token is still valid it hasnt expired but your cookie has expired youll be logged out of the client. Instead of storing session tokens in a cookie that is automatically sent on every request as one would in a traditional request-response style app Meteor stores session tokens in localStorage after users log in.
We use it for logging in via email and SMS notifications. So with this example all users will be automatically logged out after 1 day of using your app. 6 61 65 66 67 68 69 610 611 612 7 Desktop Apps expired login token FAQID_2311.
Automatically log in a user if a valid unexpired single-use authToken is present in the URL. I found no functionality available to do this even though token objects are stored with a timestamp so Id like to suggest having something available as follows. This article is valid for DocuWare versions.
If Meteor resumes the login automatically the user data may stay out of date until the resume token expires. Login tokens never expire needs to be solved by some background process maybe just a simple setInterval call The user document grows without bounds might still be a problem even with said background process in case someone logs in and out very frequently. If not do the above and return the token to the client.
Normally when the Meteor client connects to the server the first thing it does is pass the login resume token to re-establish a previous login. A login method is a method which on success calls thissetUserIdid and Accounts_setLoginToken on the server and returns an object with fields id containing the user id token containing a resume token and optionally tokenExpires. When logging in via the URL token check for the LoginToken and if its expired.
It appears that a new login token is only created when the user logs out and logs back in not when login type. I have a requirement to make login sessions expire after 24 hours and currently use the following. It would work something like this.
For Security Assertion Markup Language SAML claims users after they get their logon cookie from Active. CallLoginMethod methodArguments. If Active Directory LDAP or a local administrator account is enabled then send a POST login HTTP11 API request to retrieve the bearer token.
As I was working on understanding the process for expiring logon cookies recently I found what seemed like a big problem. However when these callbacks from the email flow are triggered the resume token is not sent until your code signals that it has finished handling the request by calling the done function that is. Basically all the goodies youd expect and all I had to code was the actual logic of generating and checking the temporary token.
IdToken. On your next trip to IdentityServer and probably other OIDC authorities the cookie for that domain may still be valid in which case youll be automatically logged back in with no login UI presented. LoginExpiration Number The number of milliseconds from when a user logs in until their token expires and they are logged out for a more granular control.
A malicious actor that has obtained an access token can use it for extent of its lifetime. Auth0. Set to null to disable login expiration.
Just to reiterate because authentication token lifetimes are tied to the lifetime of the provider token there is still a 1 hour expiration for AAD MSA and Google. However when these callbacks from the email flow are triggered the resume token is not sent until your code signals that it has finished handling the request by calling the done function that is passed into the registered callback. If you are using one of the JWT libraries then most likely you can also pass an expiration time in the signing method options.
Thus the requirement is that your authentication is configured to issue refresh tokens usually done by requesting an offline scope in the management portal. Users can configure the timeout in minutes to expiration var emailTokenTime AccountsconfigureverifyEmailTokenExpiration. Resume such as a page refresh.
Usage Add package meteor add dispatchlogin-token Generate a token for a user server-only. On client call MeteorloginWithToken with the real token you got from _generateStampedLoginToken. Use at your own risk.
Access tokens cannot be revoked and are valid until their expiry.

Toggle Switch Between Accounts Easily Help Meteor Forums
Email Verification Token Expiration Issue 12 Meteor Accounts Github

Toggle Switch Between Accounts Easily Help Meteor Forums
How To Refresh Access Token Lightwidget

Cpu Spikes Every 10 Min Due To Accounts Base Package Help Meteor Forums

How To Implement One Time Login Help Meteor Forums
Accounts Package Loginexpirationindays Option Not Working Issue 5121 Meteor Meteor Github
Solved Download Access Token Data From The Genesys Pure Alteryx Community

Find The Current Session Id In Meteor Js Stack Overflow
Github Dispatchme Meteor Login Token Automatically Log In A User If A Valid Unexpired Single Use Authtoken Is Present In The Url
Token Expired While Password Reset Issue 9798 Meteor Meteor Github